Biography
I am a Ph.D. candidate in the Department of Computer Science and Engineering, the Hong Kong University of Science and Technology, supervised by Prof. Qian Zhang. My research interests include privacy and security in wireless sensing and Reconfigurable Intelligent Surface aided wireless sensing. I received my B.S. degree in Electronic and Information Engineering from Huazhong University of Science and Technology in 2020.
Research Interest
- Wireless Sensing
- Security and Privacy
- Reconfigurable Intelligent Surface (RIS) aided Sensing
- IoT
Selected Research Projects
mmTremor: Practical Tremor Monitoring for Parkinson’s Disease and Essential Tremor in Daily Life (Oct. 2023 - Sep. 2024)
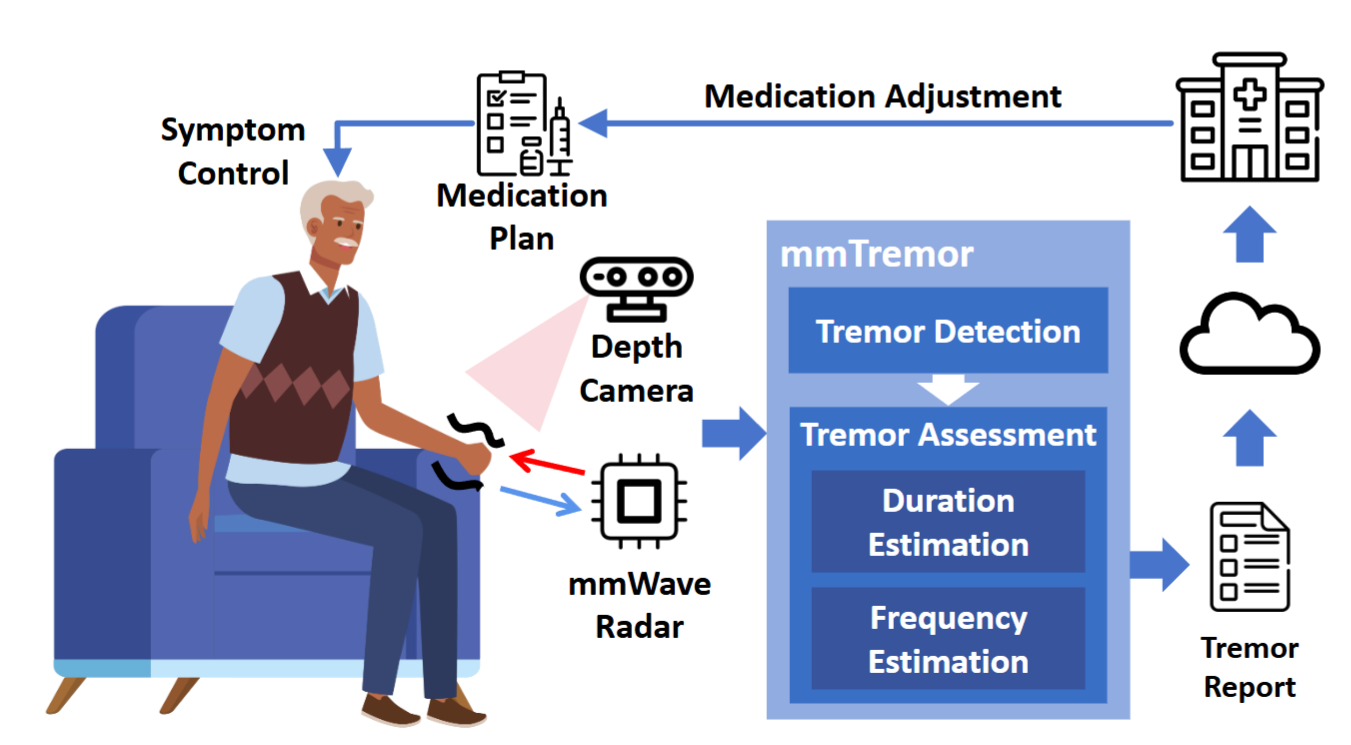
- Integrate the depth camera with the mmWave radar to enable thorough tremor movement detection at both micro and macro levels.
- Propose a joint tremor source separation scheme and a multimodal model architecture.
- Design an unsupervised contrastive adaptation for robust tremor detection.
- Collected a dataset of 28 patients and 9 healthy subjects in over 20 diverse environments.
High-resolution mmWave Imaging using Metasurface and Diffusion (May. 2024 - Aug. 2024)
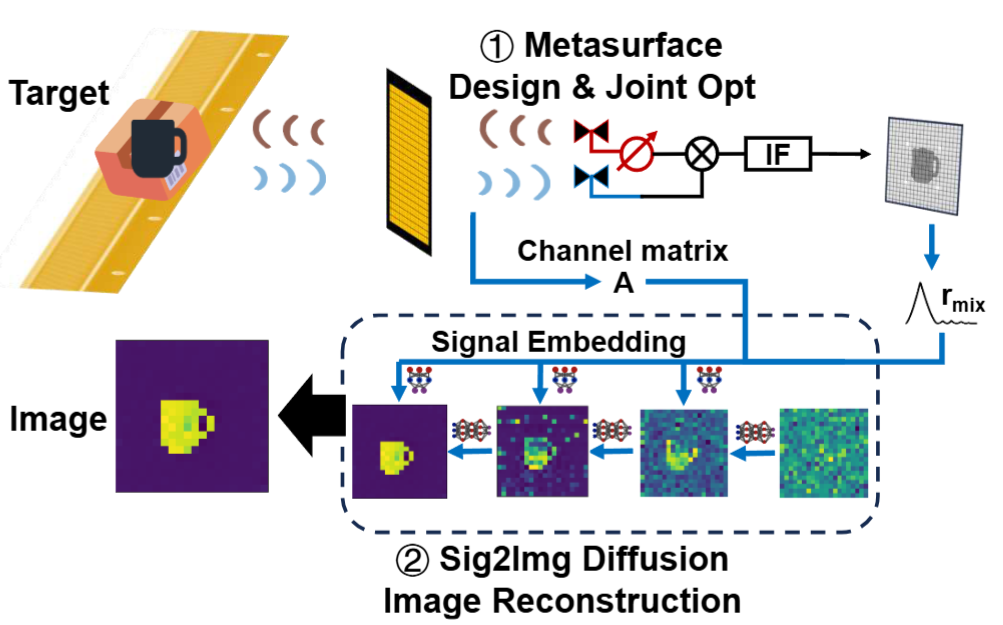
- Propose a passive metasurface for fine-resolution imaging and in 77-81 GHz.
- Design the diffusion model to replace traditional compressive sensing solvers under means squared error.
- Design an end-to-end optimization to jointly optimize the metasurface patterns, transmitter codewords, and the diffusion model.
- An efficient channel estimation method is proposed to reduce the burden of domain adaptation.
RIStealth: Practical and Covert Physical-Layer Attack against WiFi-based Intrusion Detection via Reconfigurable Intelligent Surface (Feb. 2022 - Dec. 2022)
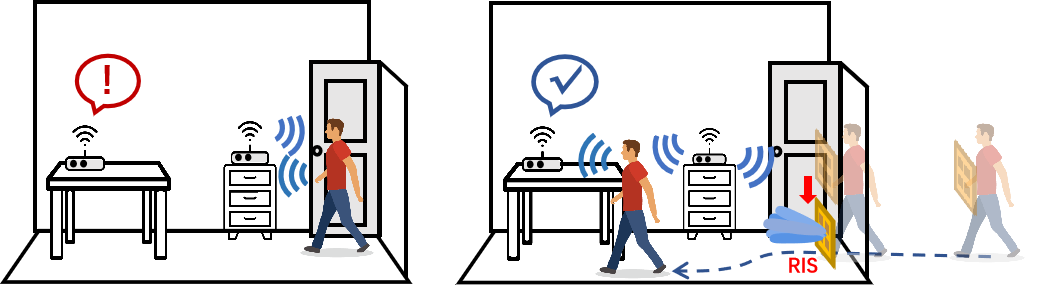
- Design a two-phase attack strategy against the practical WiFi-based intrusion detection system by analyzing the robustness improvement modules.
- Design a RIS-aided beamforming method to deflect the reflection energy away from the victim receiver to keep the intruder invisible to the system.
- Design a beamforming-based method to damage the victim system’s detection capability.
- Conduct extensive experiments to validate the attacks.
RISCan: RIS-aided Multi-user Indoor Localization Using COTS WiFi (Mar. 2022 - Nov. 2022)
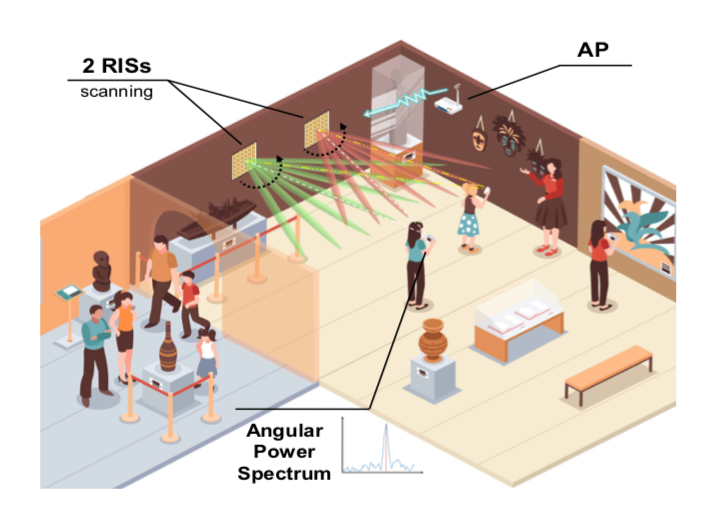
- Design a novel algorithm to extract the RIS component from the superimposed channel and design mechanisms to suppress environmental disturbance.
- Prototype RIScan with COTS Wi-Fi devices and customized RIS hardware.
- Conduct extensive experiments to demonstrate excellent performance in multi-user scenarios.
WiAdv: Practical and Robust Adversarial Attack against WiFi-based Gesture Recognition System (Nov. 2020 - Oct. 2021)
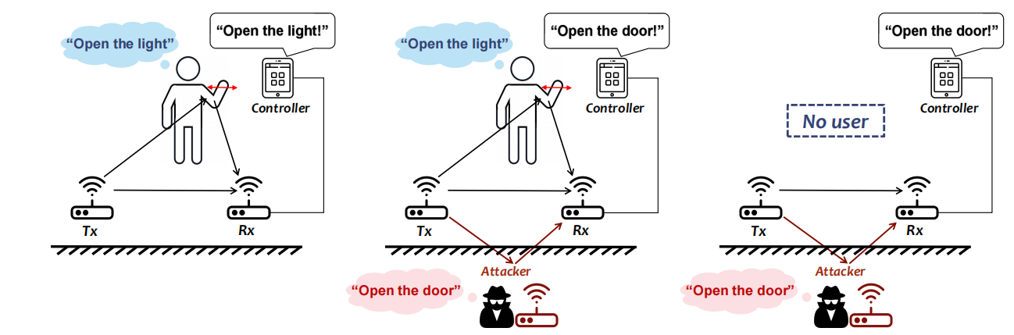
- Design a signal synthesis scheme to craft adversarial WiFi signals with desired motion features.
- Design two black-box attacks to handle the difficulties caused by non-differentiable processing modules in the sensing pipeline.
- Take the ambient interference signals and processing jitters into consideration to improve the practicality and robustness of the attack.
- Conduct extensive experiments to validate the attacks.
